A recent study has shown that many certificates are being created without proper verification. In light of this, Certificate Authorities have come to the forefront as an essential tool in ensuring the security of digital certificates. This article will discuss how Certificate Authorities can be used to vet potential breaches in the certificate-creation process.
What Is A CA?
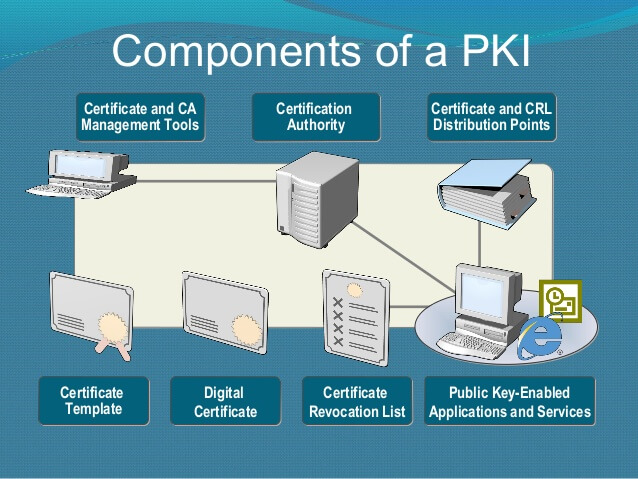
A Certificate Authority, or CA, is responsible for issuing and managing digital certificates. These certificates are used to verify the identity of individuals and businesses online, and they can be used to encrypt communication between parties. To be considered a trusted CA, an organization must meet strict guidelines set forth by international standards, such as the Internet Engineering Task Force (IETF) and the International Telecommunication Union (ITU).
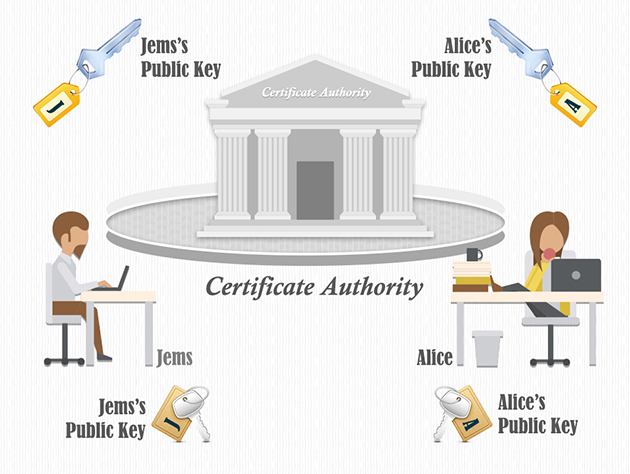
Digital certificates are based on a technology called Public Key Infrastructure, or PKI. PKI certificates contain a public key and a private key. The public key can be freely shared, while the private key must be kept secure. When two parties wish to communicate securely, they can use each other’s public keys to encrypt their messages. These messages can only be decrypted by using the corresponding private key. PKI certificates are often used in conjunction with X.509 certificates. X.509 is a format for digital certificates initially developed by the IETF. X.509 and PKI certificates are both used to verify the identity of individuals and businesses online.
There are many different types of Certificate Authorities, but they all serve the same primary purpose: to help individuals and businesses verify their identity online. Understanding how CA’s work can help keep your information safe when communicating with others online.
How Do CAs Work To Vet Potential Breaches In Digital Certification Creation?
CAS uses various methods to vet potential breaches in the digital certification process. One standard approach is called Certificate Revocation Lists, or CRLs. CRLs are lists of
certificates that the CA has revoked. When an organization wants to revoke a certificate, it must first add it to the CRL. The CRL is then published so other organizations can check it before accepting a credential. This helps to prevent certificates from being used after they have been revoked.
Another standard method CAs to vet potential breaches is Certificate Transparency, CT. CT is a system that allows CAs to log all certificates that they issue. These logs are publicly available; anyone can check them to see if a trusted CA has published a particular certificate. This helps prevent credentials from being used without the owner’s knowledge.
CAs also use various methods to vet potential breaches in digital certification creation. These methods include Certificate Pinning, Domain Validation, Extended Validation, and OCSP Stapling. By using these methods, CAs can help ensure that certificates are only used by the intended recipient and are not being used for malicious purposes.
What Are The Benefits Of Using A CA?
Using a CA to vet potential breaches in digital certification creation has many benefits. One benefit is that it helps to ensure that the intended recipient only uses certificates. This prevents credentials from being used for malicious purposes. Another advantage is that it helps to ensure that certificates are not being used after being revoked. This helps prevent organizations from having their information compromised by revoked certificates.

CAs also help to ensure that digital certification creation processes are as secure as possible. By using various methods to vet potential breaches, CAs can help ensure that certificates are only used for their intended purpose. This helps to protect businesses and individuals from having their information compromised by malicious actors.
Overall, the benefits of using a CA to vet potential breaches in digital certification creation processes are numerous. By using a CA, businesses and individuals can help to ensure that their information is safe and secure. Additionally, CAs can help to protect businesses and individuals from having their data compromised by malicious actors.
Final Thoughts
Overall, CAs play a vital role in helping to keep businesses and individuals safe online. Understanding how CAs work can help keep your information safe when communicating with others online. Additionally, by using a CA to vet potential breaches in digital certification creation, you can help to ensure that certificates are only used for their intended purpose. This helps to protect businesses and individuals from having their information compromised by malicious actors

